DASCTF下半年赛_reverse
DASCTF2025下半年比赛逆向题。前一阵子一直在复习备考,没及时更新~~
androidfff
先用jadx看,发现MainActivity是空的,然后看了下AndroidManifest发现是flutter,用blutter恢复。
blutter安装教程:https://www.cnblogs.com/hansa/p/18337467
先用blutter解包得到符号表那些,ida打开libapp.so,导入符号表
直接搜索flag找到对应的函数,这里就是密文
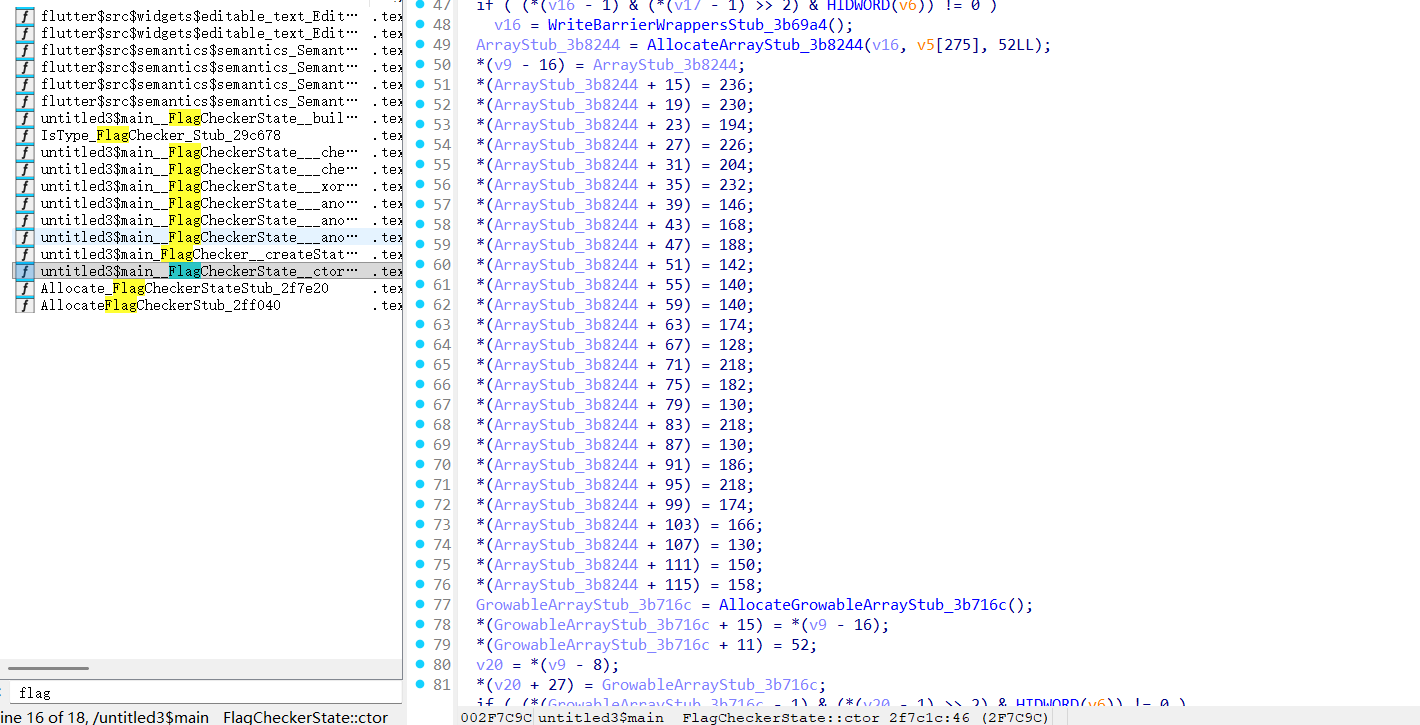
不过找到主要加密逻辑还是有点麻烦,这里我看了其他师傅的解题过程
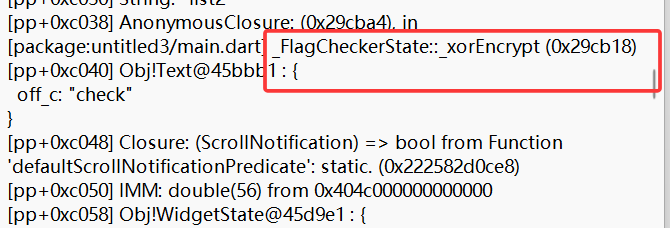
通过解包出来的pp.txt找到逻辑,地址就是0x29cb18
这里是xor加密的逻辑,先2,2相当于左移1位,解密就是右移移1位,再xor0x32,
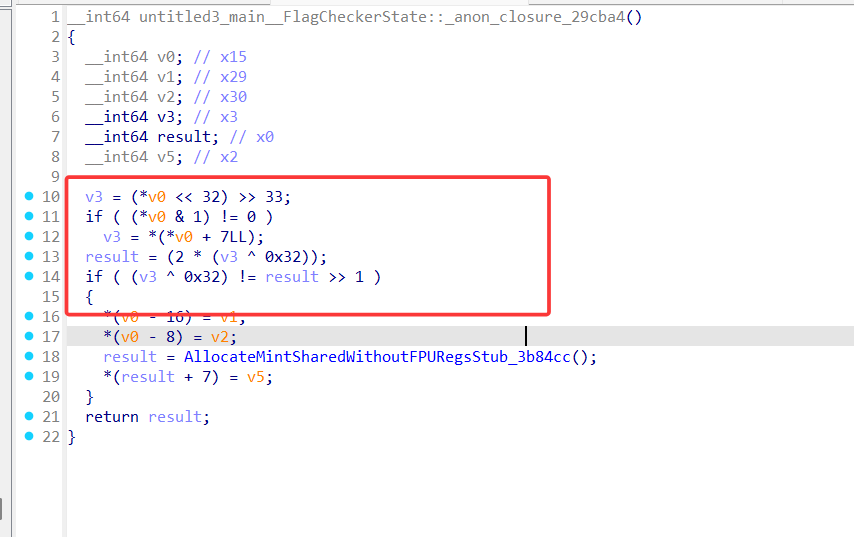
解密脚本:
1 | |
//DASCTF{flutter_is_so_easy}
ezmac
这里找到验证的部分,输出right/wrong
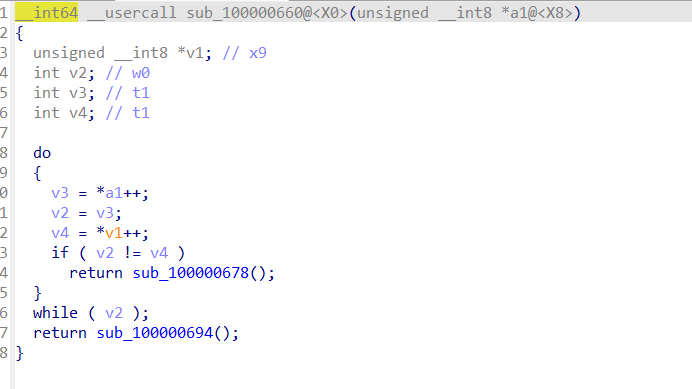
然后看看上级的调用,看汇编,这里其实是传参的过程,传参是0x57,其实就是xor加密的密钥
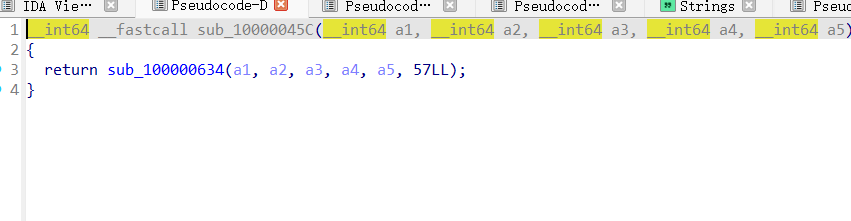
byte_100004022就是密文内容
这里就是xor加密部分
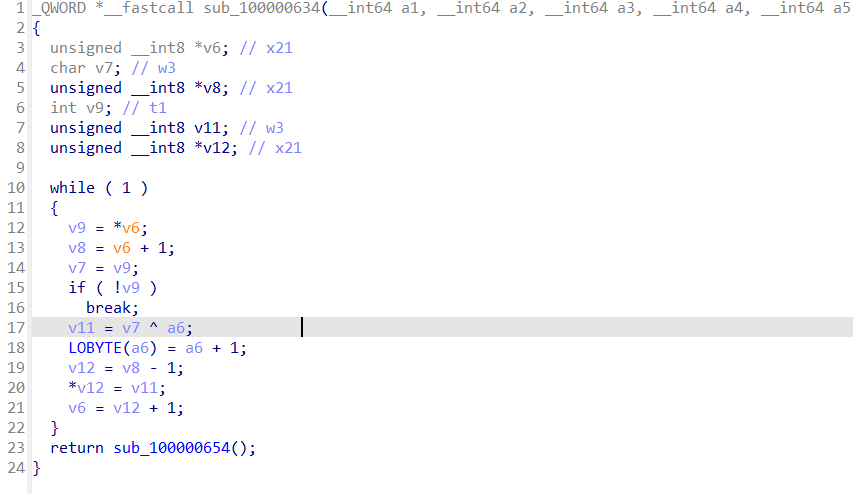
解密脚本
1 | |
androidfile
直接看mainactivity,发现所有的明文内容都被加密了,不过影响不大
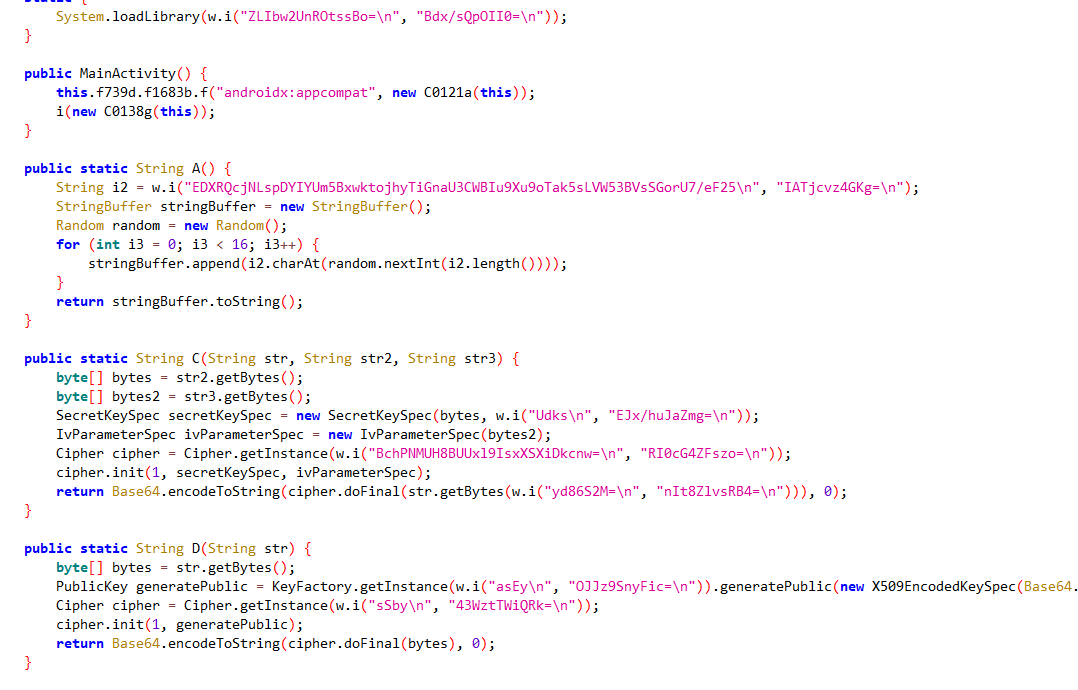
加密过程:先将flag进行AES-CBC加密,不过key和iv都是伪随机的,再进行base64加密,然后是RSA公钥加密,再base64加密,最后是在native层的校验。
解密就清晰了,先看so文件,native层的加密就是rc4+base64,rc4加密密钥就是REVERSE
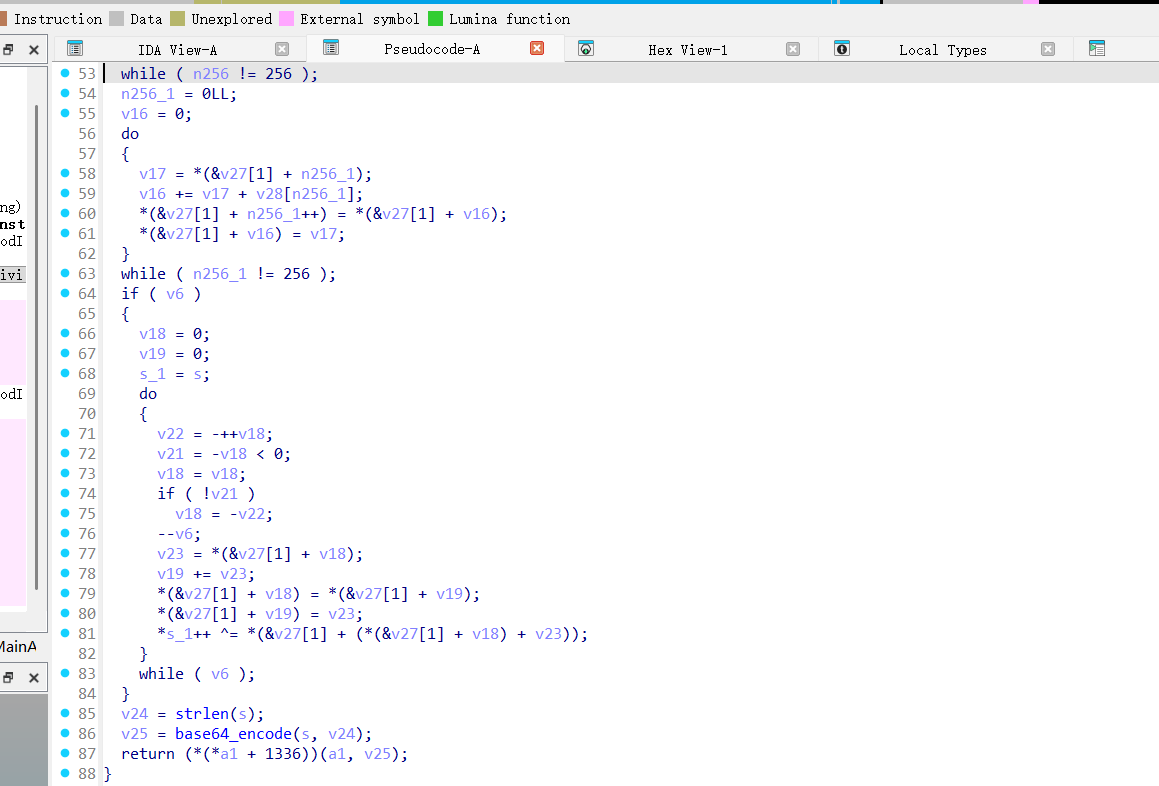
题目给的密文等信息
1 | |
提取第一段密文进行解密
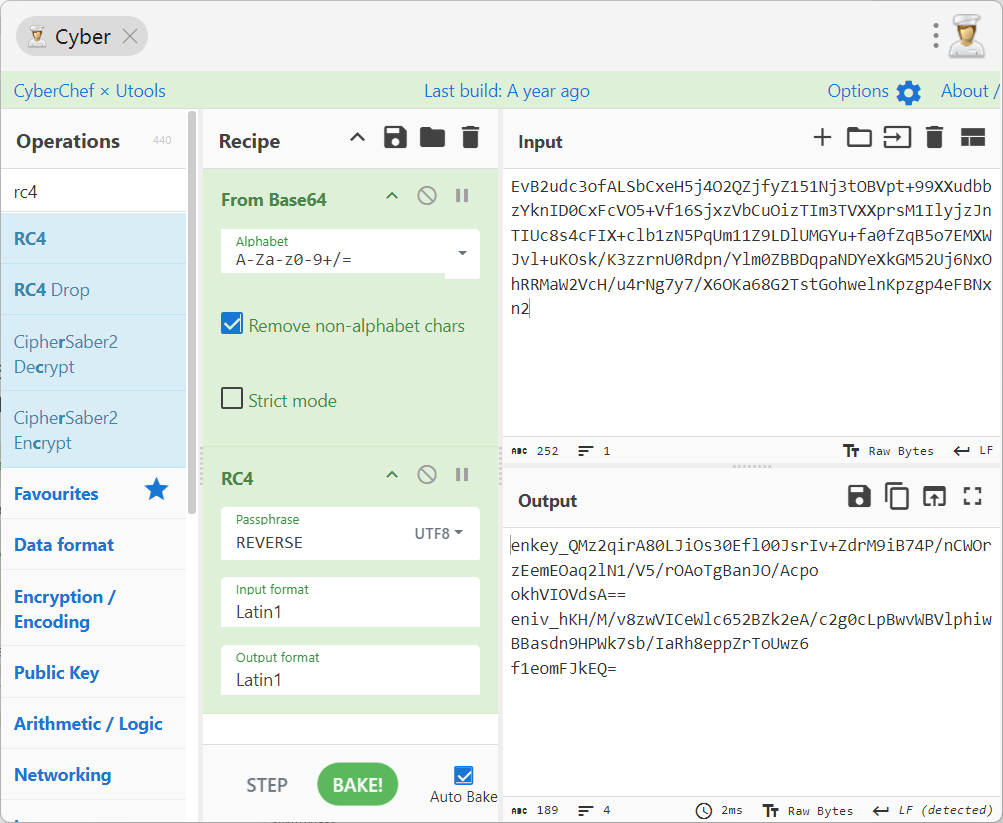
1 | |
这是解出来的key和iv,下一步就是利用rsa来解密key和iv了,
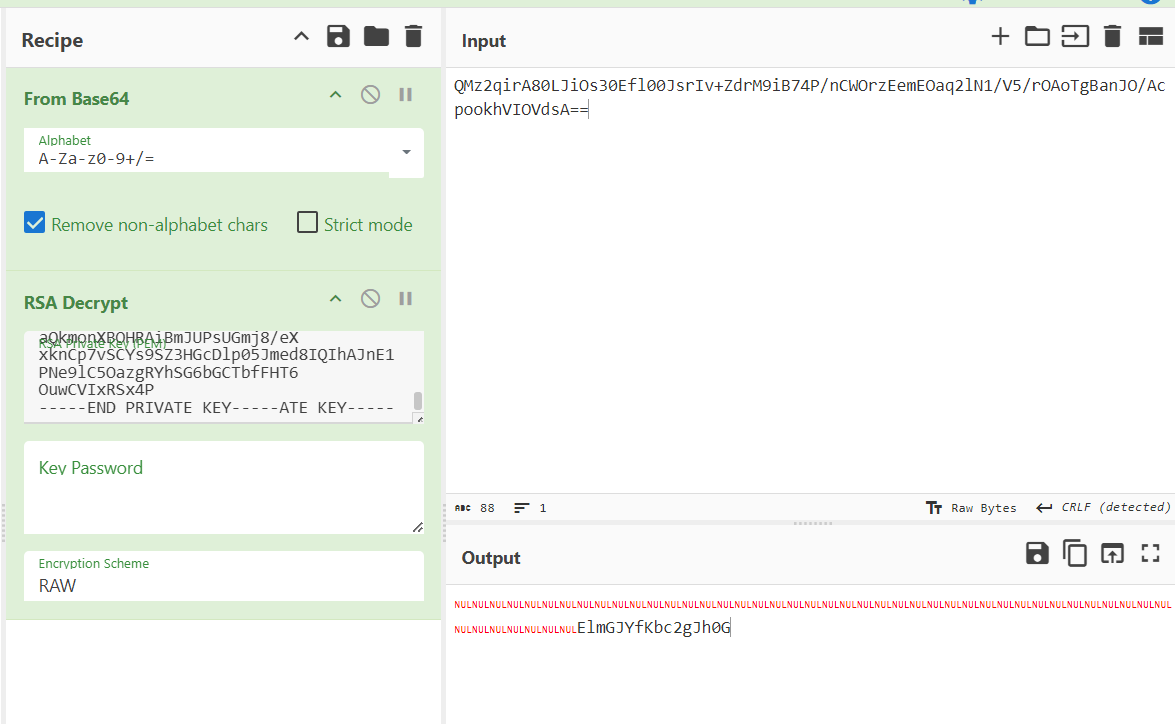
key:ElmGJYfKbc2gJh0G
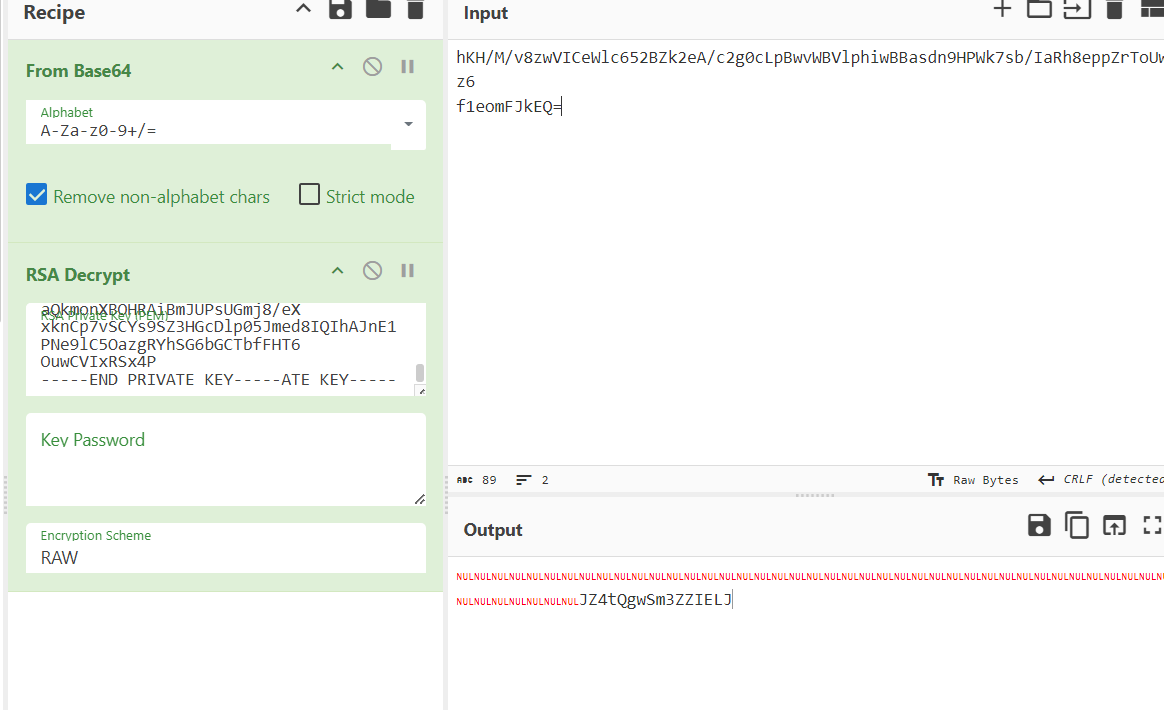
iv:JZ4tQgwSm3ZZIELJ
最后就是aes解密
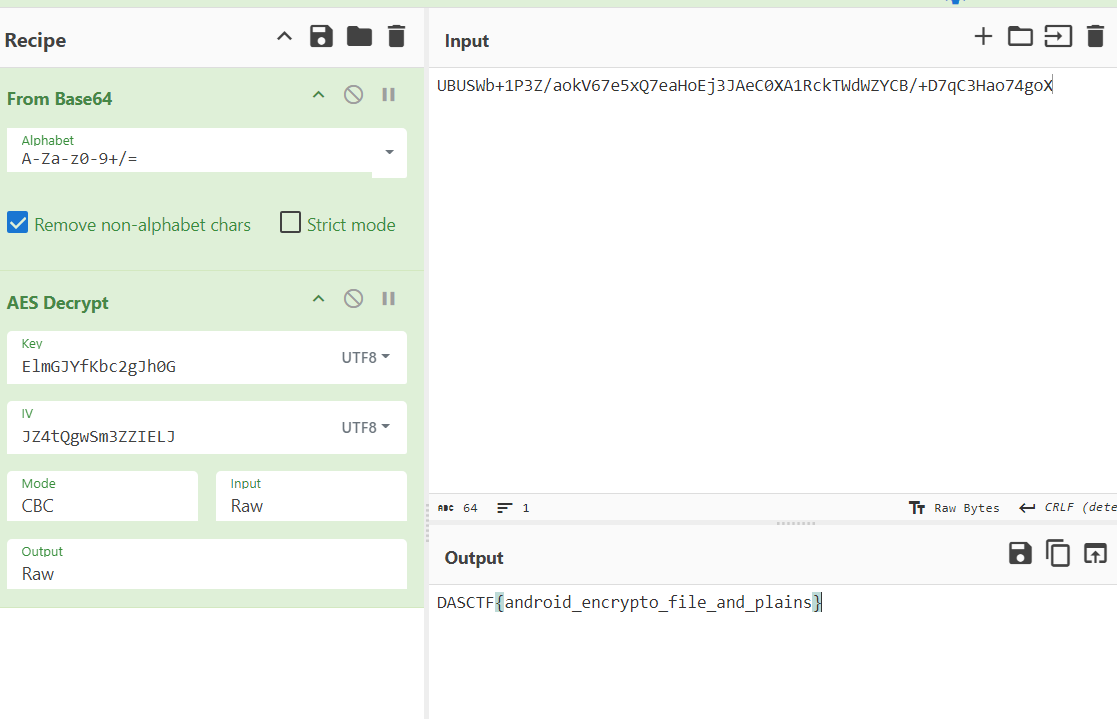
DASCTF{android_encrypto_file_and_plains}
login
在server端,这里是接收了一个account然后进行验证,byte_C1A0是对比的密文,属于rsa密文
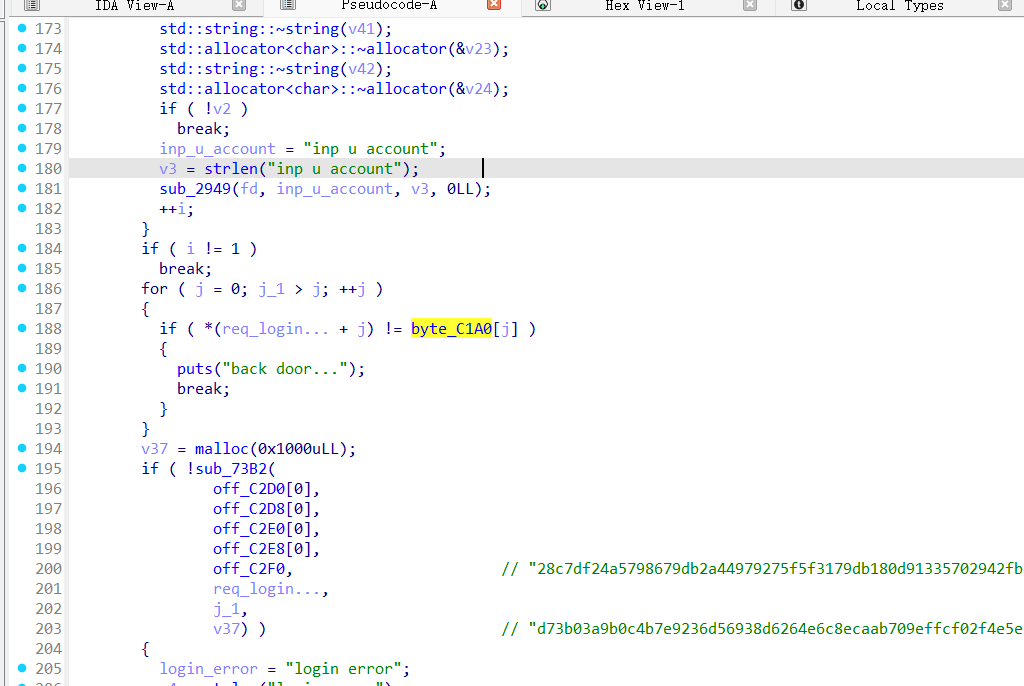
还有一个rc4加密
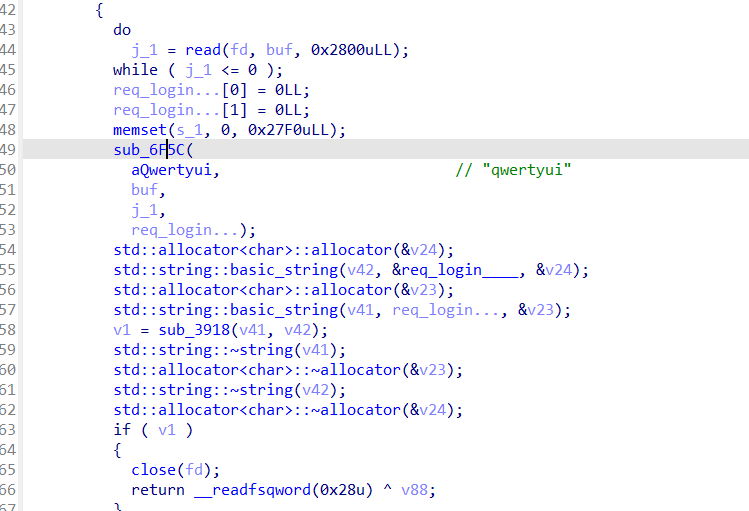
sub_73B2使用rsa私钥解密
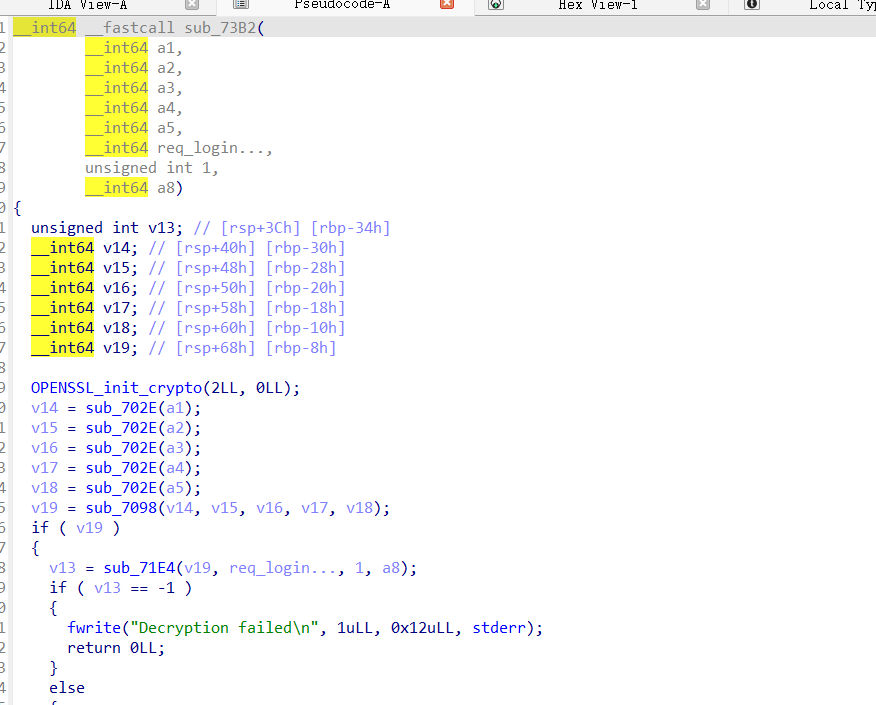
在client端中获取RSA因⼦(P,Q)重建私钥解密byte_C1A0和byte_C0A,解密得到key和iv
1 | |
sub_49DD 和 sub_4125 函数都是AES-CBC加密
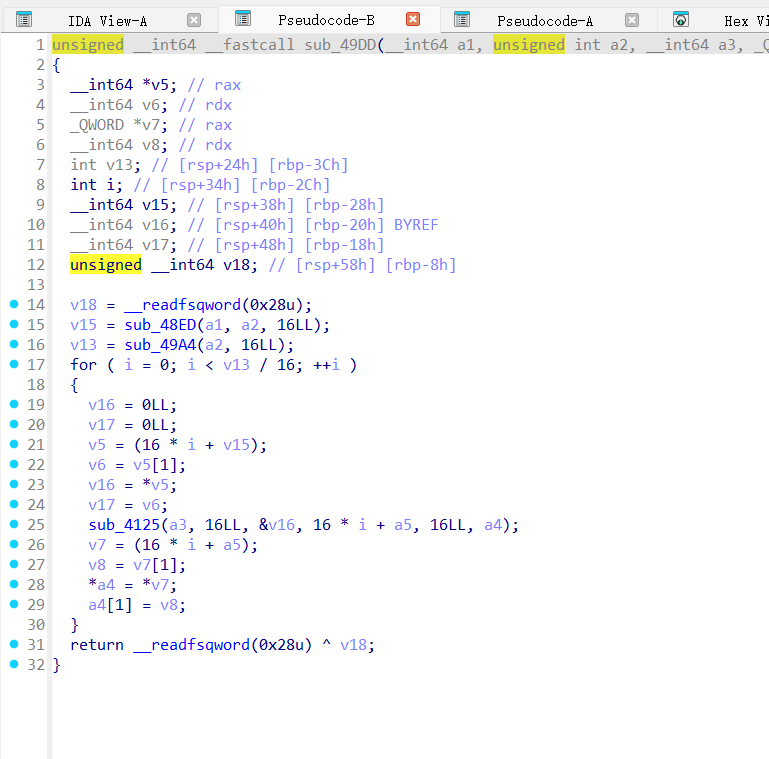
解密脚本
1 | |
iv: aassddffgghhjjll
Key: qqwweerrttyyuuii
aes解密
1 | |