2025强网拟态mobile
2025强网拟态mobile
just
前言
这题当时想着试试能不能做出来,在比赛的时候差在最后加载il2cpp.so那边。现在想来看来是大晚上做题做的昏头转向了,找的文章都找错了自己还没发现,这个表情包来表达一下我现在复现的心情吧。
解题过程
总的来说这题解题过程也是相当复杂,大晚上做的时候甚至忘了前面做了什么。
之前接触了的一道是基于windows下的il2cpp的unity逆向题,这道是基于apk文件,有点不同。主要的思路是提出apk文件中的il2cpp.so文件,然后底下的思路就是基本解题思路了。
这道题对il2cpp.so文件进行了加密,解压之后看到的libil2cpp.so文件是加密之后的,仔细分析libjust.so文件找到加密逻辑就可以。
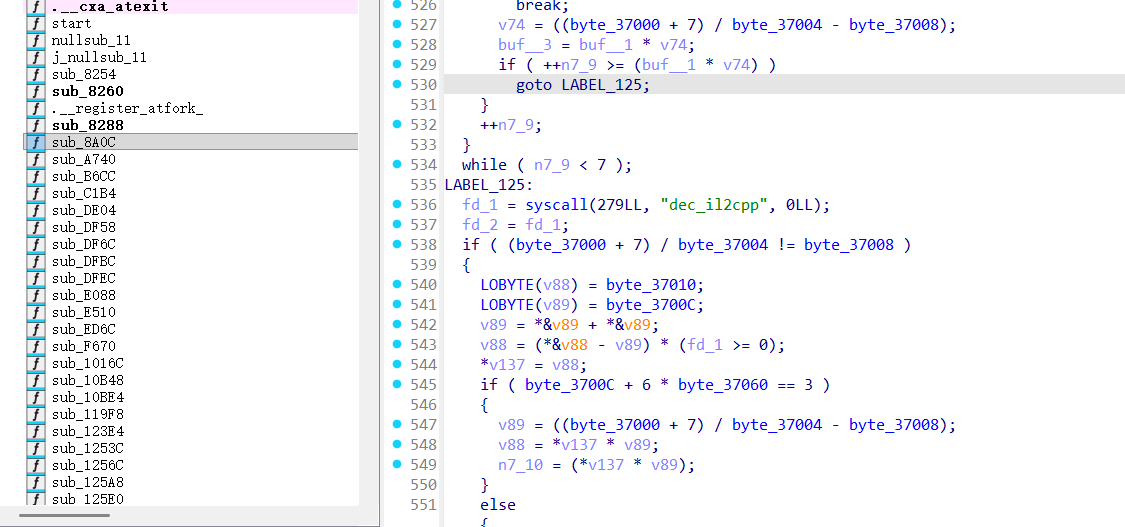
这边我就是从初始函数开始往下找关键函数的,然后发现了这里,dec_il2cpp这,我感觉就是主要的加密逻辑,理解一下发现这里果不其然就是,基于rc4的加密,密钥是nihaounity,注意^0x33
1 | |
以上脚本解密之后得到decil2cpp.so,下一步按理说就是解包global-metadata.dat,看看加载decil2cpp.so能不能发现什么
定位到sub_211B8C函数,这里尝试优先加载 game.dat,失败则 fallback 到 global-metadata.dat,然后调用了sub_211D94函数,也加载了 global-metadata.dat,跟进看他的内容
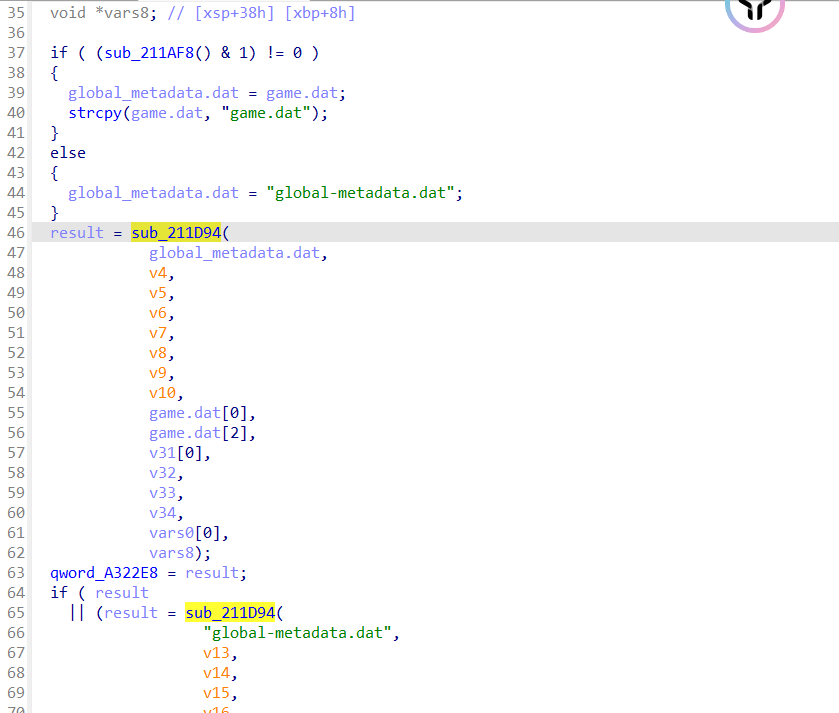
global-metadata.dat 是 Unity IL2CPP 编译时生成的二进制元数据文件。
它包含了所有 C# 类型、方法、字段、字符串的定义信息。
运行时必须加载它才能支持反射、序列化、跨语言调用等功能。
这个函数载入了metadata,在这里找找看加解密逻辑
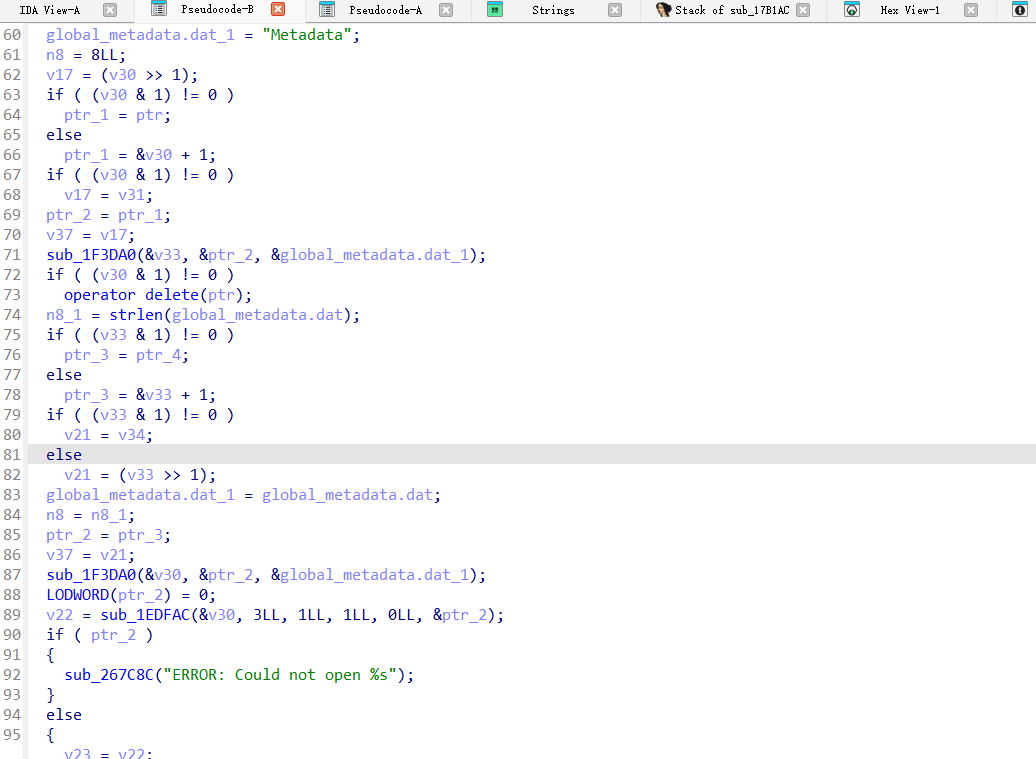
定位到sub_21A2C8函数,这个函数是对global-metadata.dat 数据进行解密。
解密脚本还原global-metadata.dat
1 | |
接下来解包得到的global-metadata.dat
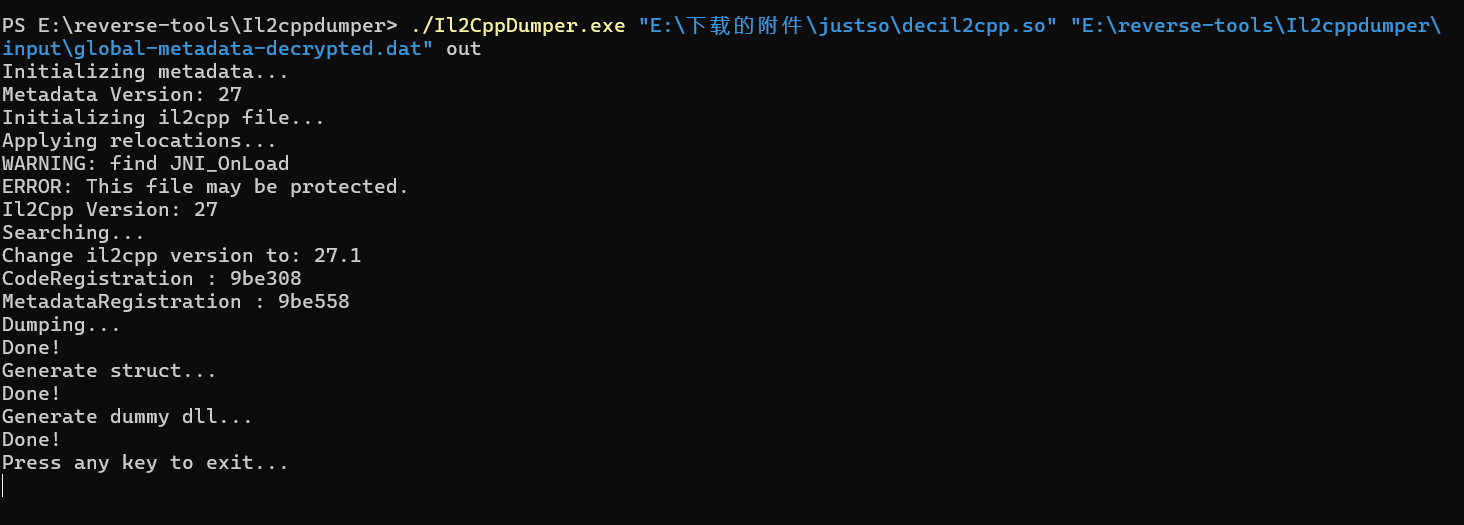
在decil2cpp.so附加 ida_py3.py 和 script.json 文件来恢复符号表。
这里我在比赛的时候做的时候加载的是 Assembly-CSharp.dll,也就是开头说的问题。Assembly-CSharp.dll可以用dnspy看,能看到主要的加密验证函数那些,但是最重要的代码内容还是得着重分析il2cpp文件。
加载好之后找到flagcheck函数,这里的加密主要是先进行字节转换然后再调用tea加密
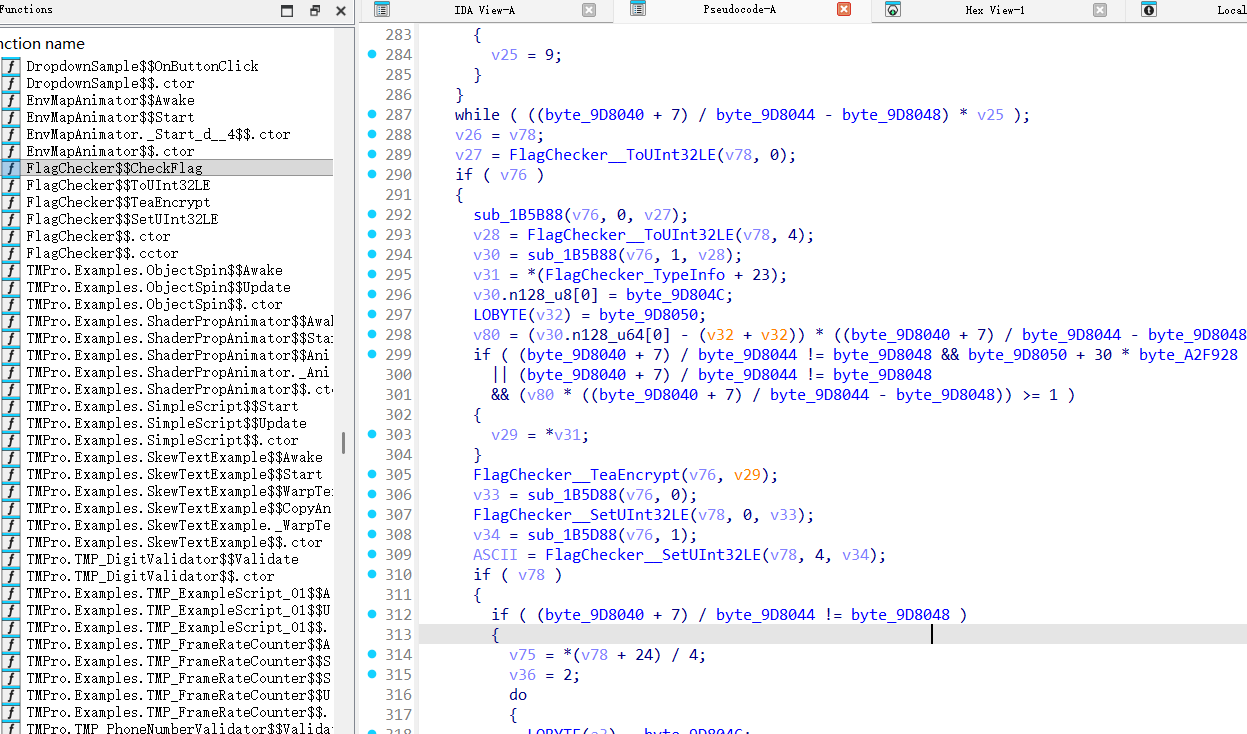
密文密钥是可以通过动调提取的,我没有环境可以调试,看了其他大佬的wp学习一下
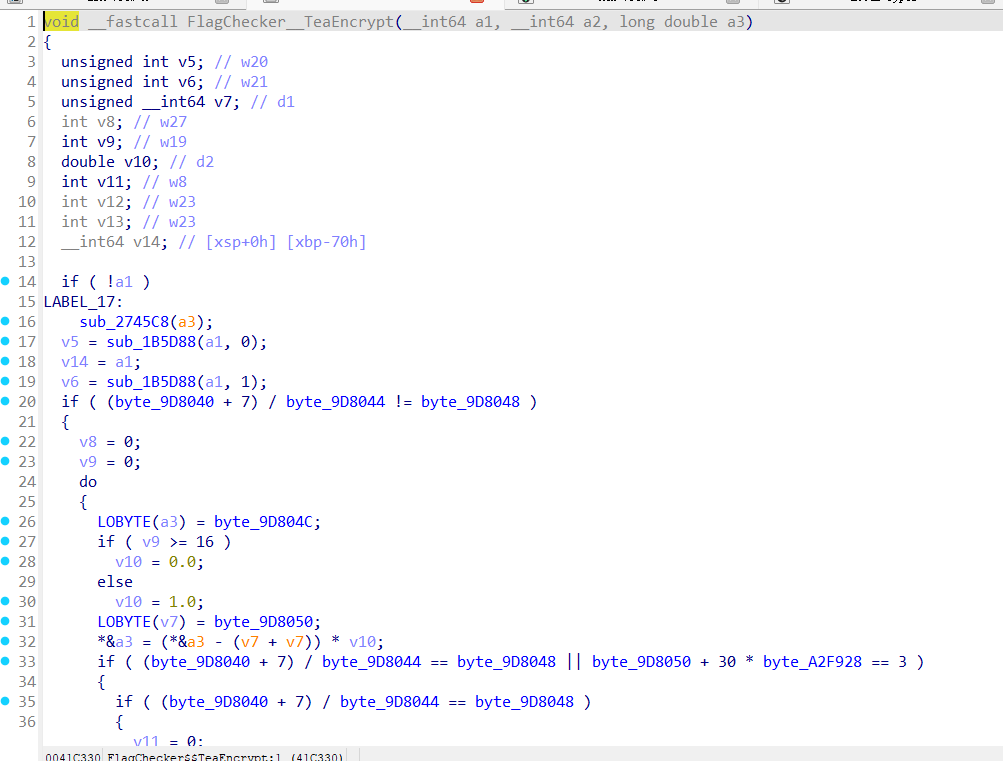
FlagChecker$$.cctor在这里数据会进行初始化,在类加载时,把内嵌的静态数组(key 和密文)初始化成内存中的运行时对象。
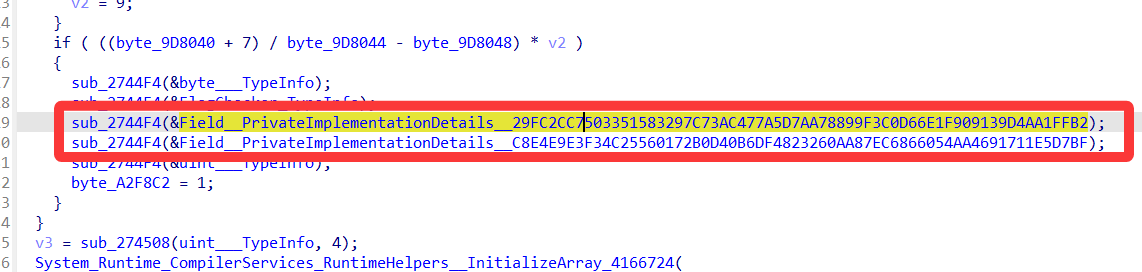
这两个符号名是 .NET / IL2CPP自动生成的静态数组字段名,key数组是16字节,密文数组是40字节。
接下来就可以从dump.cs里找到对应密文密钥的偏移量,我直接搜字符串就可以定位
1 | |
确定偏移 是0xF901D 和 0xF9045,然后利用偏移读取global-data.dat 里的密文密钥内容
1 | |
得到密文密钥:
1 | |
1 | |
EZMiniAPP
先查看一下发现没用加密过
然后用wxappUnpacker解包一下,
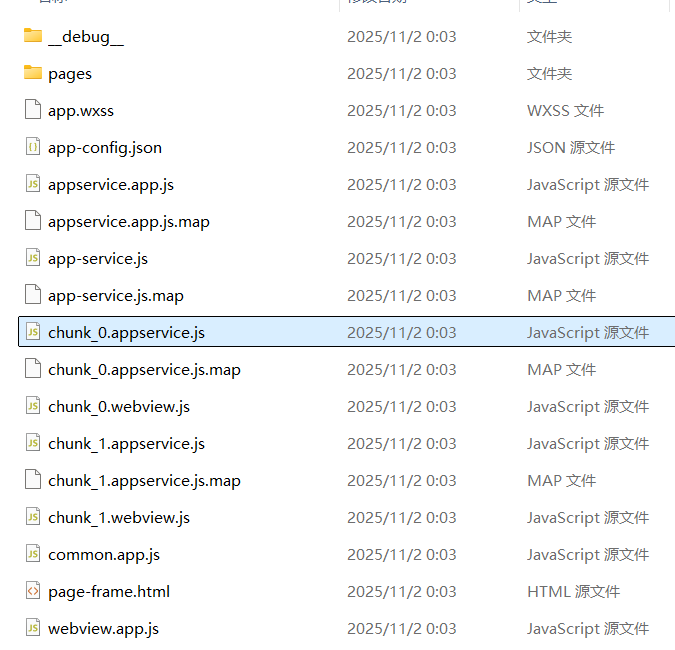
在chunk_0.appservice.js中发现主要加密内容
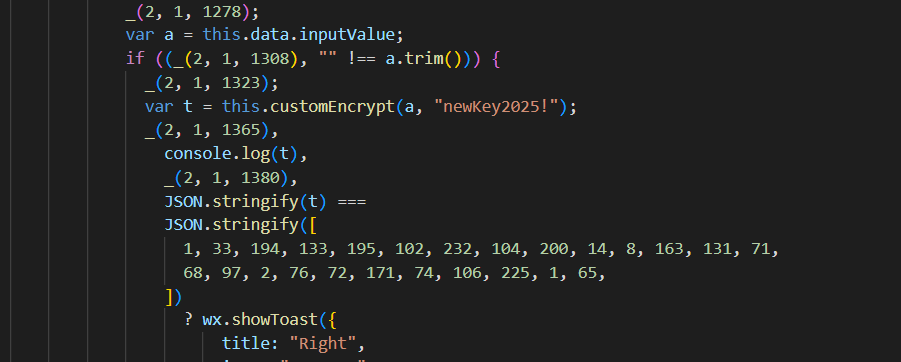
密钥:newKey2025!
密文:[ 1, 33, 194, 133, 195, 102, 232, 104, 200, 14, 8, 163, 131, 71, 68, 97, 2, 76, 72, 171, 74,106, 225, 1, 65 ]
enigmaticTransformation(a, t)是实际的加密函数:
1 | |
解密脚本:
1 | |