1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
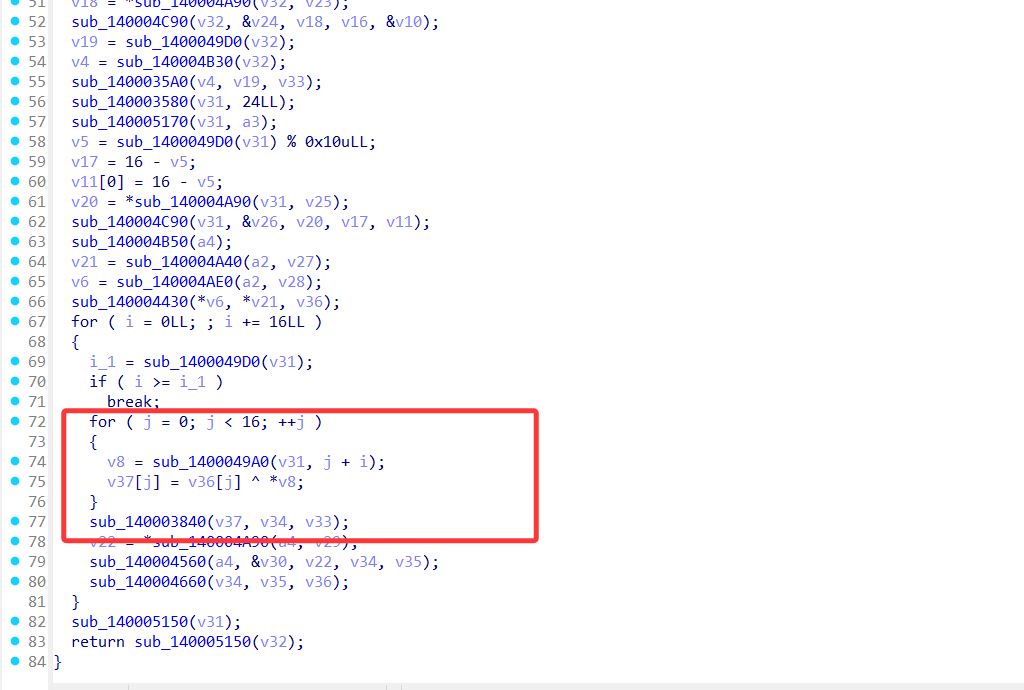
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
| import struct
w = 32
r = 20
def ROTL(x, y):
return ((x << (y & (w-1))) | (x >> (w - (y & (w-1))))) & 0xFFFFFFFF
def ROTR(x, y):
return ((x >> (y & (w-1))) | (x << (w - (y & (w-1))))) & 0xFFFFFFFF
S_char = bytes([
0xE0, 0xAA, 0x68, 0x73, 0x7D, 0xCD, 0x54, 0x72, 0xE2, 0xAA,
0xD4, 0xFA, 0x41, 0x0C, 0x03, 0x9C, 0x51, 0xCA, 0x72, 0x5D,
0xF4, 0x53, 0xCA, 0xAD, 0x25, 0xEF, 0x26, 0x13, 0x8F, 0x14,
0xC1, 0x48, 0x40, 0x26, 0x1C, 0x0D, 0x6D, 0x91, 0x32, 0x16,
0xF8, 0xFC, 0x4F, 0xB5, 0xF9, 0x5F, 0x2C, 0x97, 0xEC, 0x64,
0x34, 0x6B, 0xB3, 0xFD, 0xB4, 0x89, 0xBE, 0xA5, 0x2D, 0x51,
0x04, 0x37, 0x18, 0x85, 0xB3, 0x88, 0x0D, 0xB8, 0x52, 0x05,
0x8E, 0xCD, 0x8C, 0xD8, 0xB3, 0x4F, 0x74, 0x81, 0xA6, 0xE2,
0xDF, 0x35, 0x68, 0x40, 0xA5, 0x1A, 0x49, 0x53, 0x05, 0x7C,
0x44, 0x53, 0xFA, 0xCB, 0x4F, 0xDB, 0xD8, 0xDC, 0x04, 0x31,
0x22, 0xF9, 0xD6, 0xB9, 0x6E, 0x1F, 0x53, 0xE5, 0x4E, 0xB6,
0x30, 0xAB, 0xA0, 0x4B, 0x7B, 0xC8, 0x7E, 0xB1, 0x21, 0x98,
0xDC, 0xAA, 0xFB, 0xB0, 0xC2, 0x72, 0x39, 0xD8, 0x11, 0xFE,
0x81, 0x7C, 0xE0, 0x6E, 0xBC, 0x99, 0x68, 0x6A, 0xA1, 0xBA,
0xA9, 0xED, 0x8E, 0x15, 0x5B, 0x20, 0x58, 0x2A, 0xCC, 0xB1,
0x85, 0xC9, 0xE3, 0x0B, 0x21, 0xD7, 0x7B, 0xBF, 0x5B, 0x5D,
0xC2, 0x76, 0xEB, 0x64, 0xD8, 0xC8, 0xE3, 0x44, 0x5F, 0xC7,
0xDF, 0xD9, 0x8D, 0x23, 0x1C, 0x54
])
S = [struct.unpack("<I", S_char[i*4:i*4+4])[0] for i in range(len(S_char)//4)]
def rc6_decrypt_block(block):
A, B, C, D = block
C = (C - S[2*r+3]) & 0xFFFFFFFF
A = (A - S[2*r+2]) & 0xFFFFFFFF
for i in range(r, 0, -1):
A, B, C, D = D, A, B, C
t = ROTL(B * (2*B + 1) & 0xFFFFFFFF, 5)
u = ROTL(D * (2*D + 1) & 0xFFFFFFFF, 5)
C = ROTR((C - S[2*i+1]) & 0xFFFFFFFF, t) ^ u
A = ROTR((A - S[2*i]) & 0xFFFFFFFF, u) ^ t
D = (D - S[1]) & 0xFFFFFFFF
B = (B - S[0]) & 0xFFFFFFFF
return [A, B, C, D]
data = bytes([
0x44,0xa0,0x93,0x6b,0x3f,0x9f,0xb7,0x2d,
0x49,0xda,0xab,0x33,0xe0,0x32,0x3a,0xb7,
0xd6,0xe6,0x32,0x22,0xc1,0xc6,0xa1,0x6b,
0xa4,0x8e,0xf4,0x7d,0x4e,0x08,0x31,0xe9,
0x9c,0xcc,0x89,0x4c,0xfb,0x3d,0x48,0xa1,
0x54,0x28,0x6c,0x8b,0x75,0x31,0xb5,0xc5
])
xor_key = b"WcE4Bbm4kHYQsAcX"
plain = b""
for i in range(0, 48, 16):
block = struct.unpack("<4I", data[i:i+16])
decrypted = rc6_decrypt_block(block)
plain += struct.pack("<4I", *decrypted)
plain = bytearray(plain)
for j in range(16):
plain[j] ^= xor_key[j]
for j in range(16, 48):
plain[j] ^= data[j-16]
print(plain.decode(errors='ignore'))
|
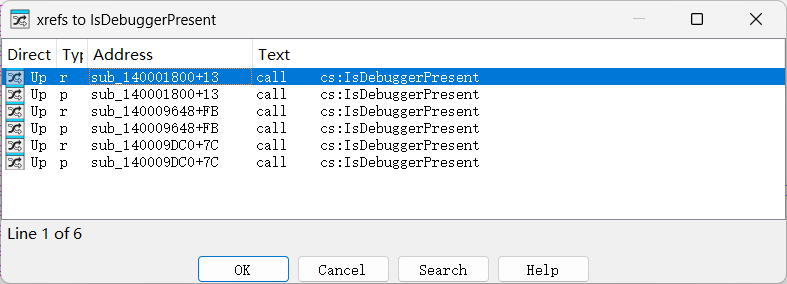
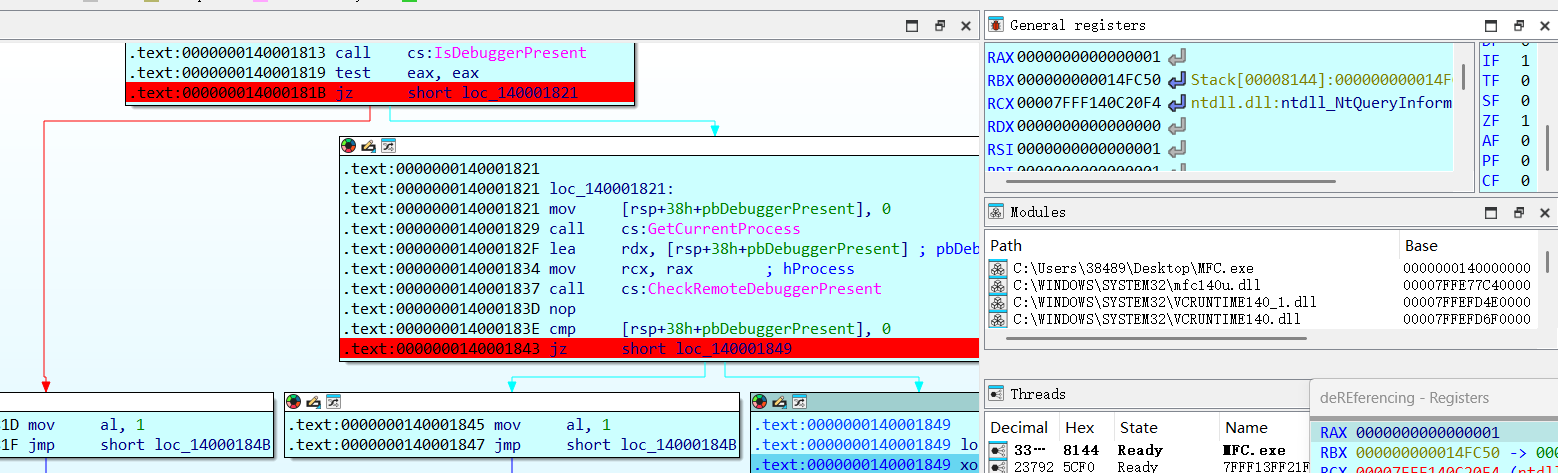
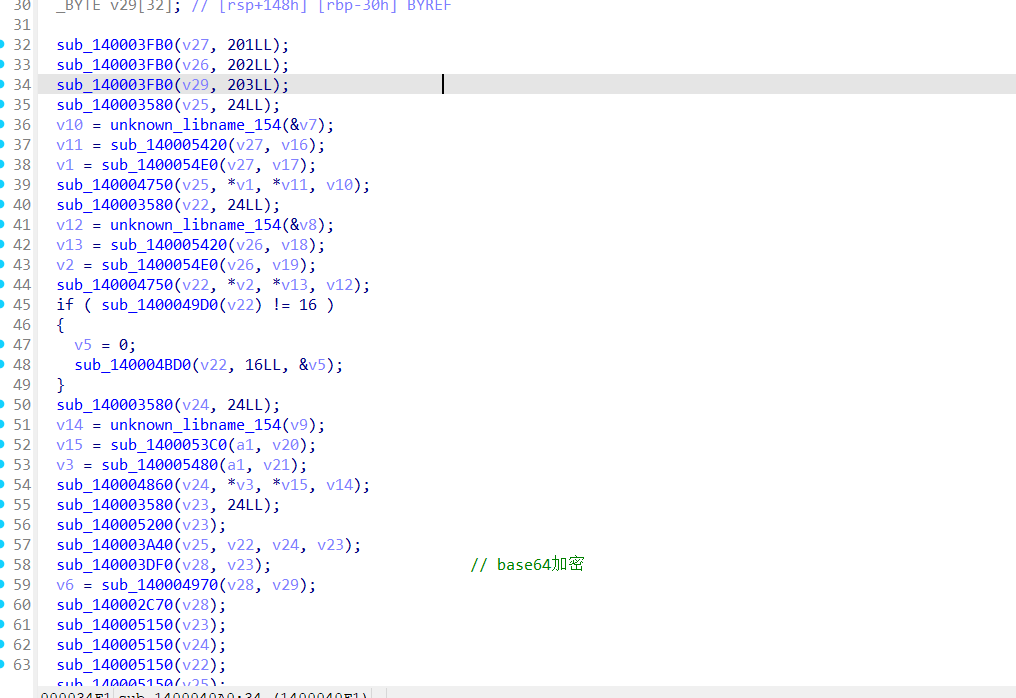
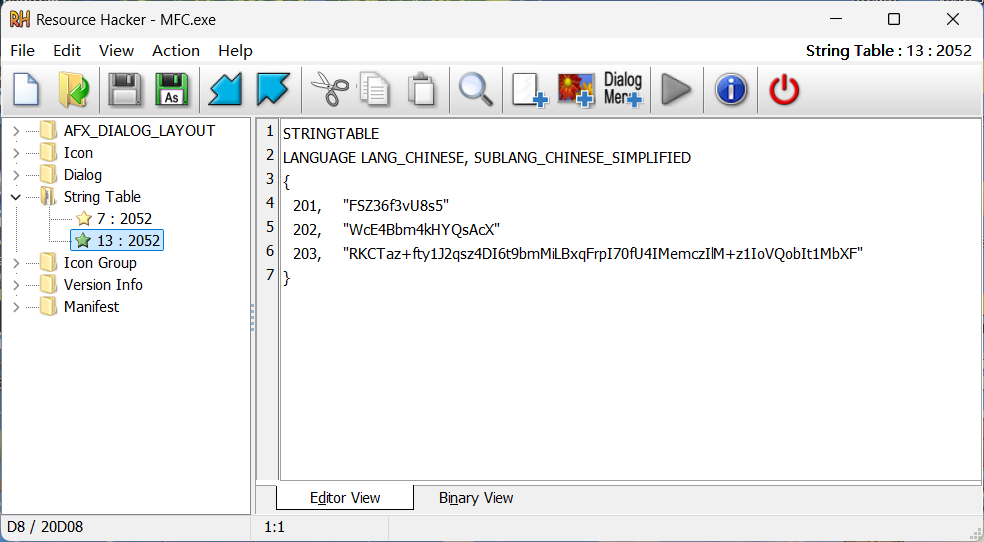
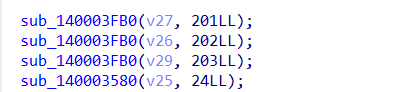 我们可以通过ResourceHacker工具找到
我们可以通过ResourceHacker工具找到