L3Hctf部分wp
TemporalParadox
写这一题用了快半天的时间www,反正得先把函数都理解透了才行
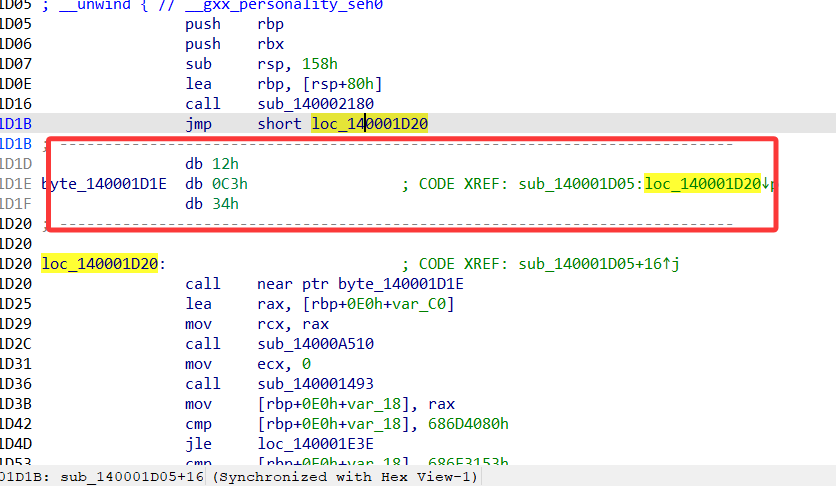
先找到主函数入口,有一个花指令,nop掉之后反编译
这里直接跳转,中间插入的就是花指令
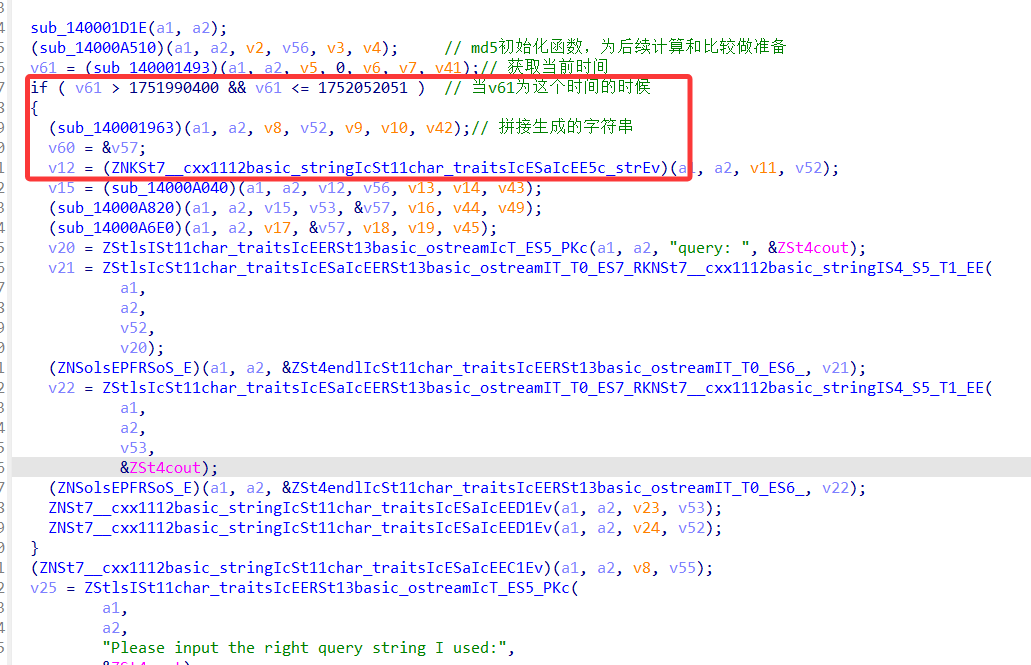
注意,以下函数运行在所给的时间节点下v61 > 1751990400 && v61 <= 1752052051,主要看sub_140001963函数
具体分析看注释
大概就是通过计算两个表达式是否相等来决定字符串的拼接,然后计算字符串的md5的值看是否与所给的密文相等
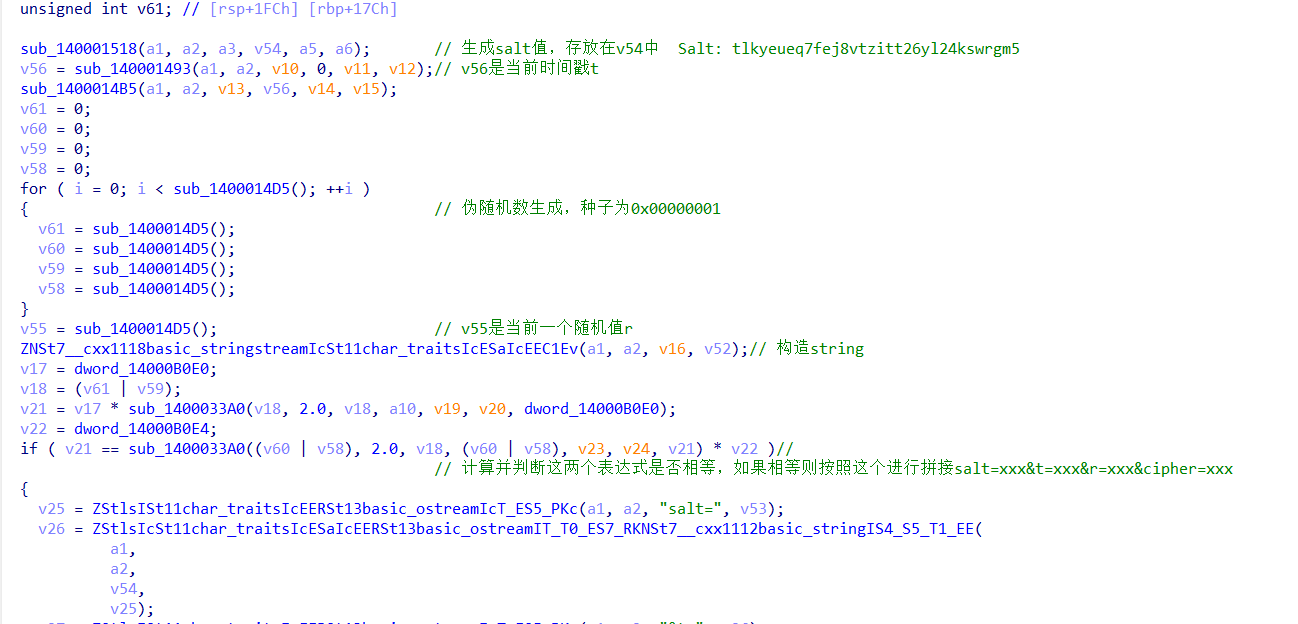
Salt: tlkyeueq7fej8vtzitt26yl24kswrgm5 固定值,通过以下代码得到
1 | |
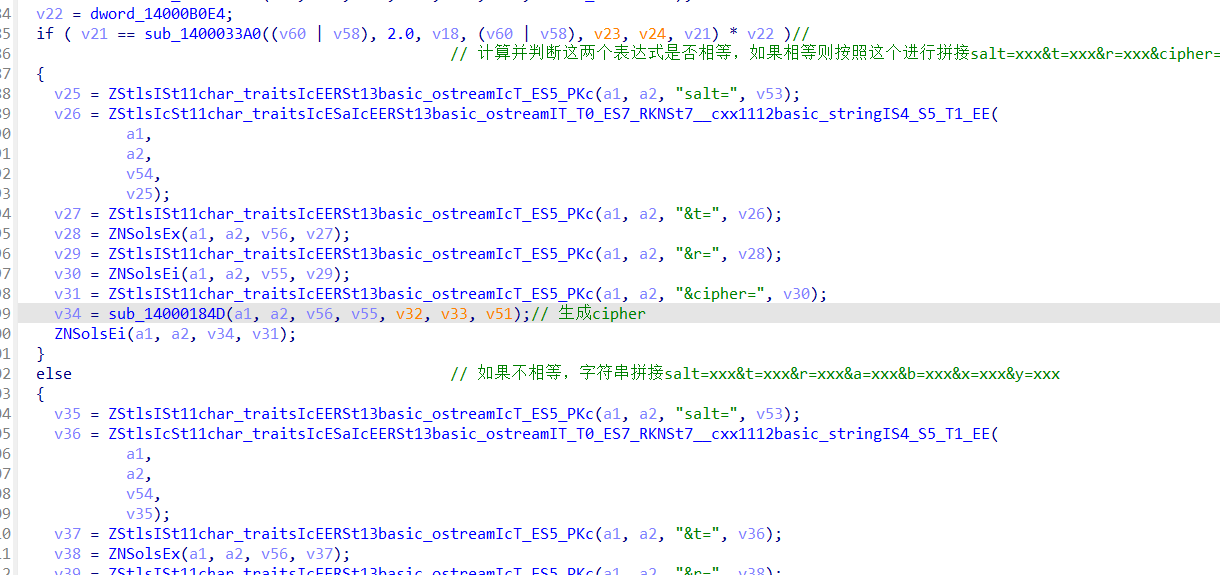
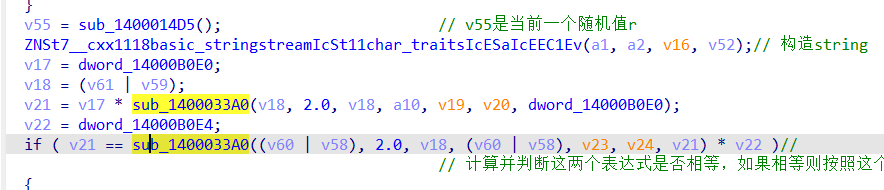
r,a,b,x,y都与随机数生成有关,cipher的生成来自于函数sub_14000184D,同时也与两个置换盒有关
第 1~3 轮每轮用 sub_1400016A0的片段 xor 进状态,再做 s盒与p盒变换。
第 4 轮取第 4 片段 XOR,再做 仅 S盒;最后取第 5 片段再 xor,返回 cipher。
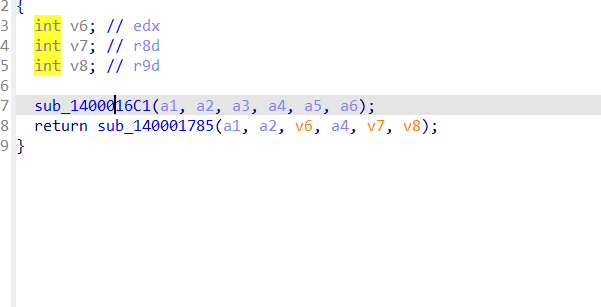
这里的判断条件也与随机生成数有关,最终可以通过爆破来实现
整个过程就可以分为字符串为salt=xxx&t=xxx&r=xxx&a=xxx&b=xxx&x=xxx&y=xxx和salt=xxx&t=xxx&r=xxx&cipher=xxx两种进行爆破(最终结果是满足salt=xxx&t=xxx&r=xxx&a=xxx&b=xxx&x=xxx&y=xxx这个字符串爆破成功)
这里贴出脚本,由于要用到openssl这个库,我直接在虚拟机上运行代码了,安装这个库也比在windows端方便多
1 | |
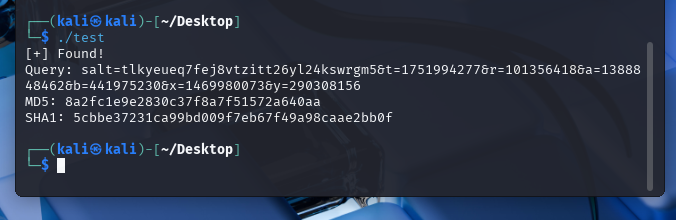
终焉之门
直接看看不到什么有用的代码,就直接动调,随便翻翻就看到了这个多层base64,解密一下hhhhh
后来知道这一段是用来循环异或加密得到主要逻辑的
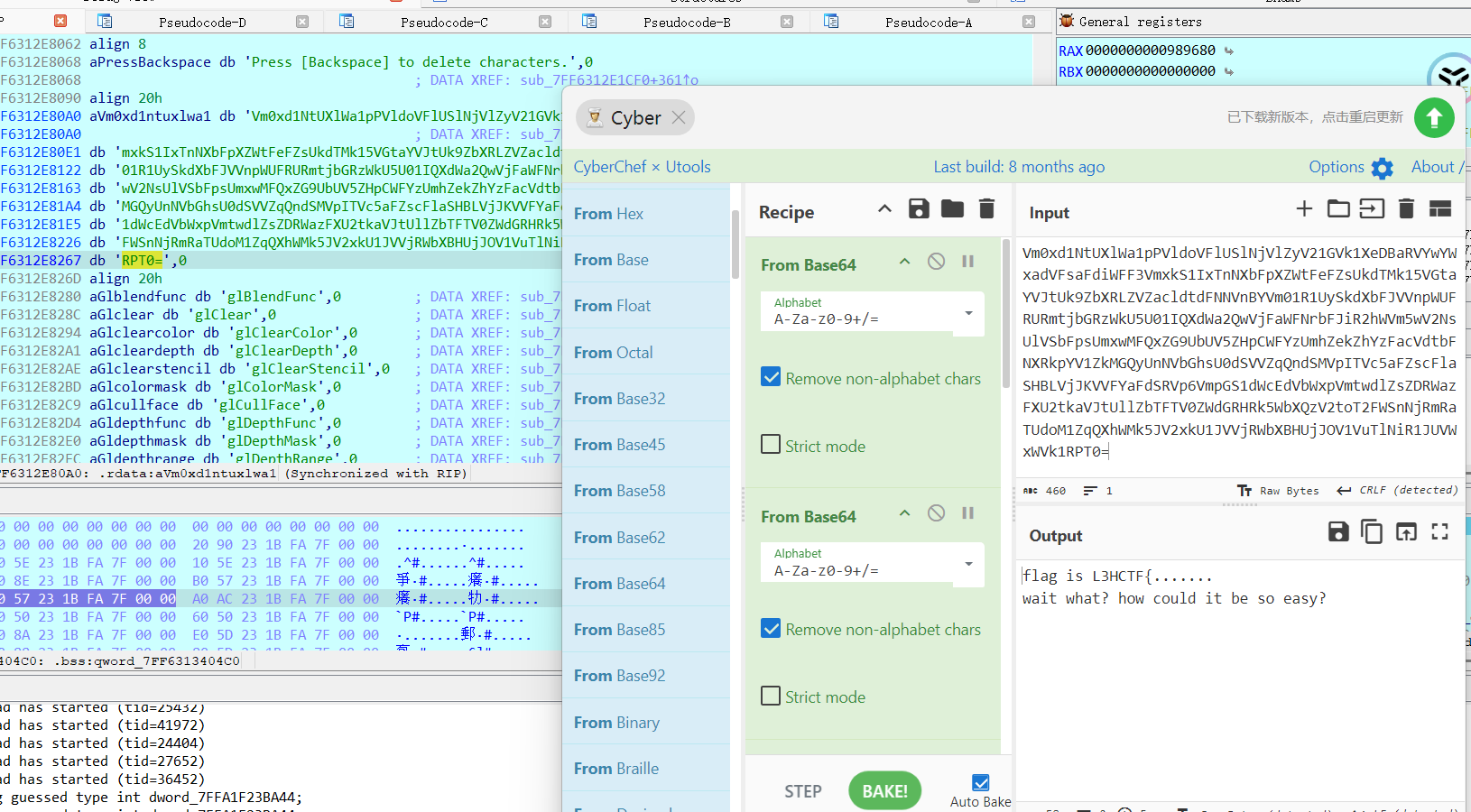
aVersion430Core动调的时候双击进去看看,主加密内容放在了.data段
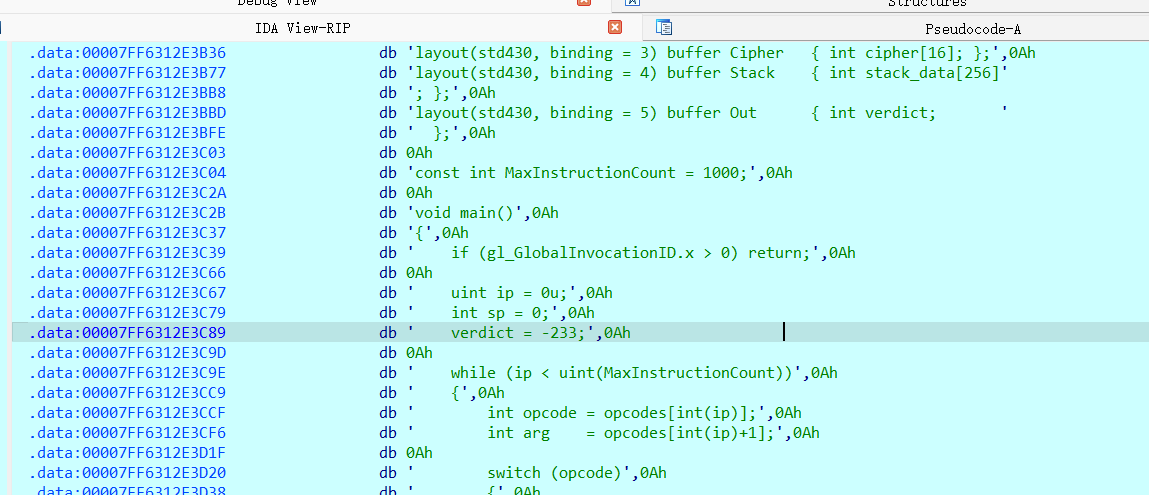
这段代码实现了一个运行在 GPU 上的简单虚拟机,通过执行opcodes中的指令序列,对栈数据进行运算
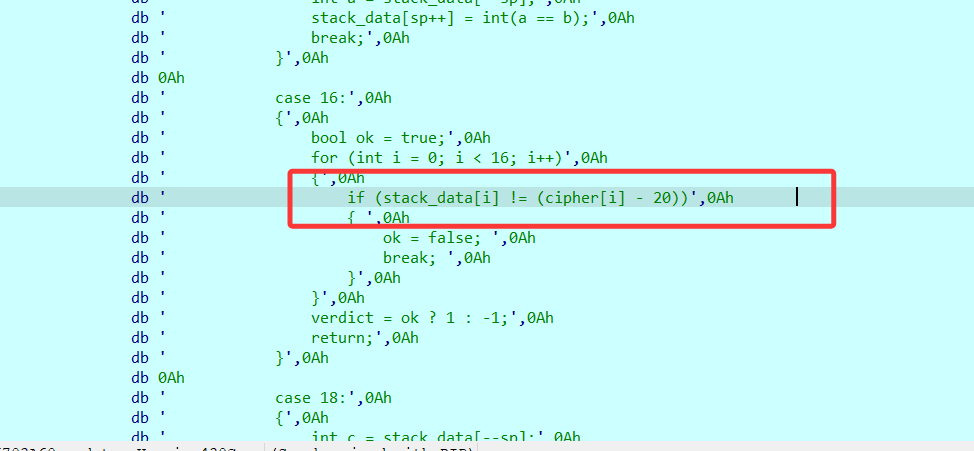
这里是核心校验
栈中的前 16 个数,必须等于 cipher[i] - 20。
还可以通过另一个方法得到主要的逻辑
我先搜索字符串,找到那么一串base64编码,然后交叉引用找到函数
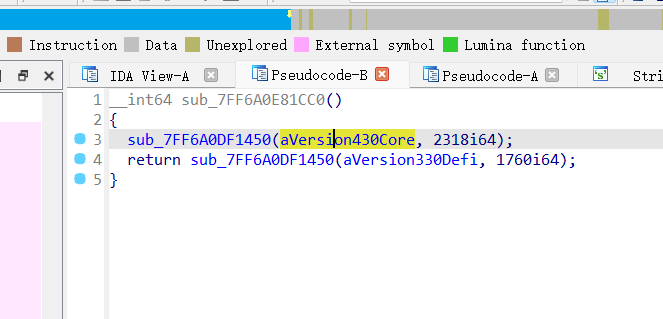
这个加密函数调用aVersion430Core的内容与base64编码进行循环异或
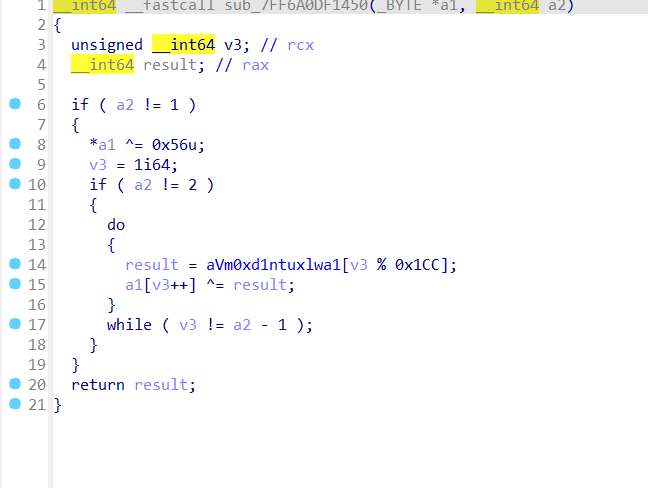
写出代码可以直接跑出内容
1 | |
从这三个地址里得到opcodes,co_consts和cipher的内容
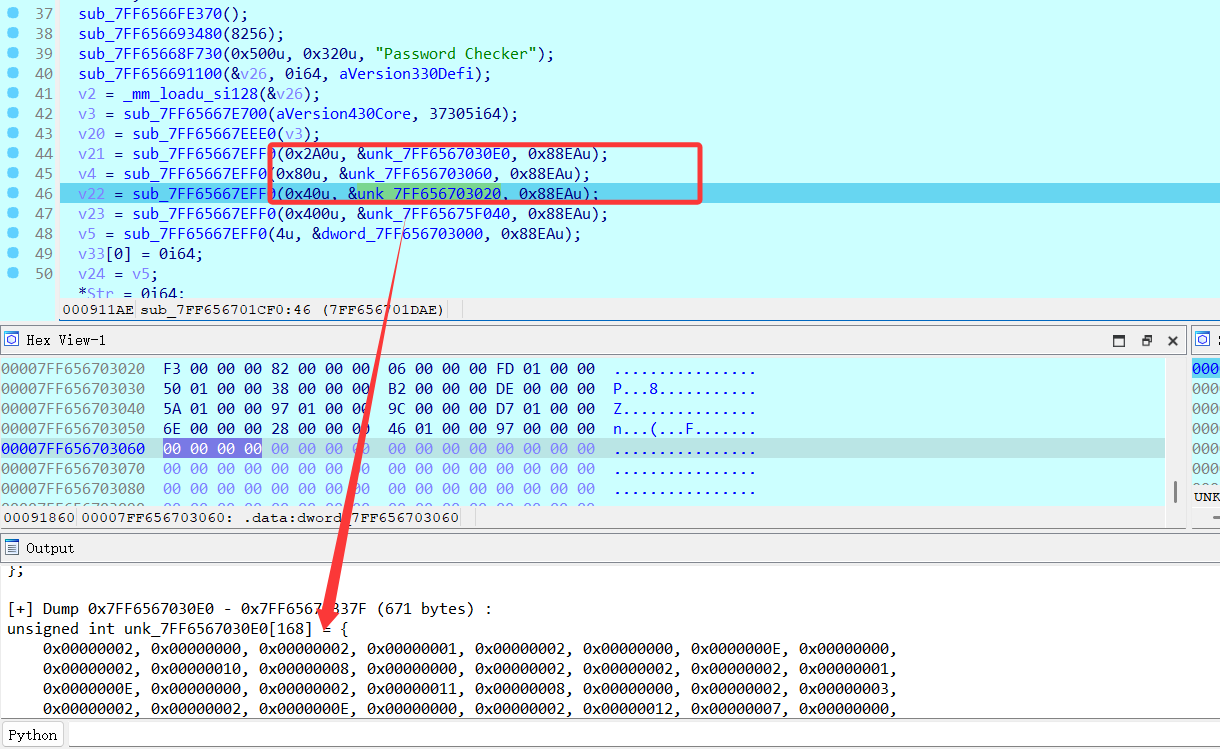
这里贴出主函数的内容以及注释部分
1 | |
得到关键信息之后,写一个解释器,看看虚拟机解释器是如何操作栈中的数据,得到加密逻辑
1 | |
过程:
每一步操作都是基于栈的,利用这三种运算异或(opcode=14)、加法(opcode=7)、减法(opcode=8),
stack [2] 的生成为例(对应目标 t2)
用户输入即co_consts的内容为x0-x15
步骤:
[IP=6] 加载 x2 到栈 stack[2] = 0xFA = x2;
[IP=7] 加载 x1 到栈 stack[3] = 0xC8 = x1;
[IP=8] 异或 stack[2] = stack[2] ^ stack[3] = x2 ^ x1;
[IP=9] 加载 0到栈 stack[3] = 0x0;
[IP=10] 减法 stack[2] = stack[2] - stack[3] = stack[2] - 0 = x2 ^ x1 。
需要满足x2 ^ x1 = t2
1 | |
最终解密代码
1 | |
ez_android
这题也是花了一天多的时间才解决QAQ,真是不容易啊,还是得好好理解,多动动脑筋嘞~
直接在com目录下找到mainactivity,发现TauriActivity,不太清楚Tauri 框架是啥
在swdd的指导下先学习一下理论知识
TauriActivity
TauriActivity 是 Tauri 框架为 Android 平台提供的桥接 Activity 类,Tauri 是一个跨平台应用开发框架(主要用 Rust 编写),允许使用 Web 技术(HTML/JS/CSS) 构建前端,同时通过 Rust 后端实现逻辑。
TauriActivity 的主要功能:
- 提供一个 WebView 容器,加载应用前端(HTML/JS)。
- 通过 JNI 调用 Rust 编译的共享库(
libtauri.so)。 - 提供文件选择、权限处理、JS ↔ Rust 通信接口。
Tauri 框架的静态资源提取方法:
先直接搜索关键词:index.html,交叉引用发现这里的包含文件名和文件位置的表
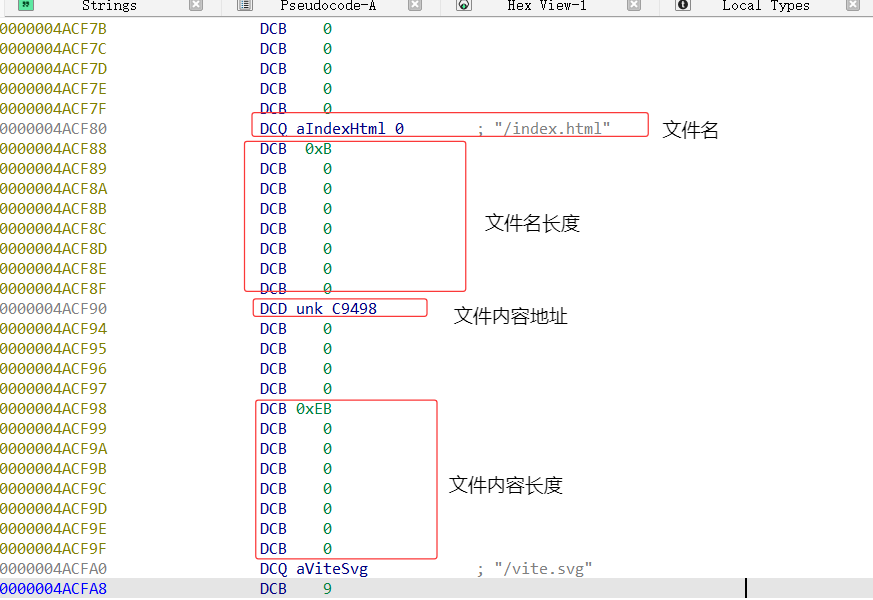
以下代码把文件内容dump出来
1 | |
由于我的idapython一直没法安装成功brotli,就先dump出来文件之后在本地解压缩
1 | |
然后就可以读取html文件内容啦
这题的解题wp:
解包apk文件之后看看有啥内容
打开assets想要找到.js文件或者.html文件,但是只有prof文件,说明前端资源被打包或者压缩了,结合tauri框架,前端文件可能被打包进rust后端可执行文件里了
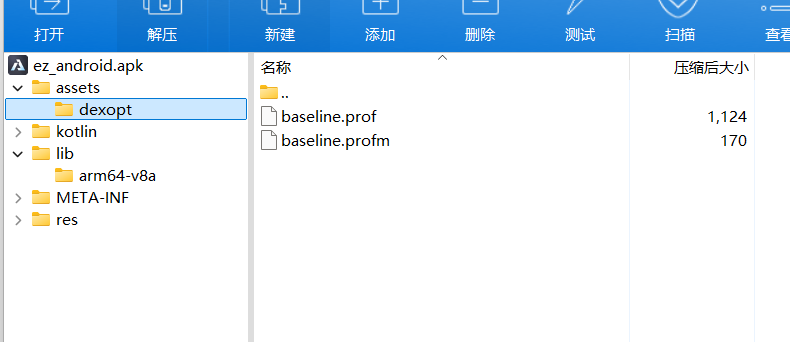
ida反编译so文件
依照上面写的静态资源提取方法,解压缩index.html内容
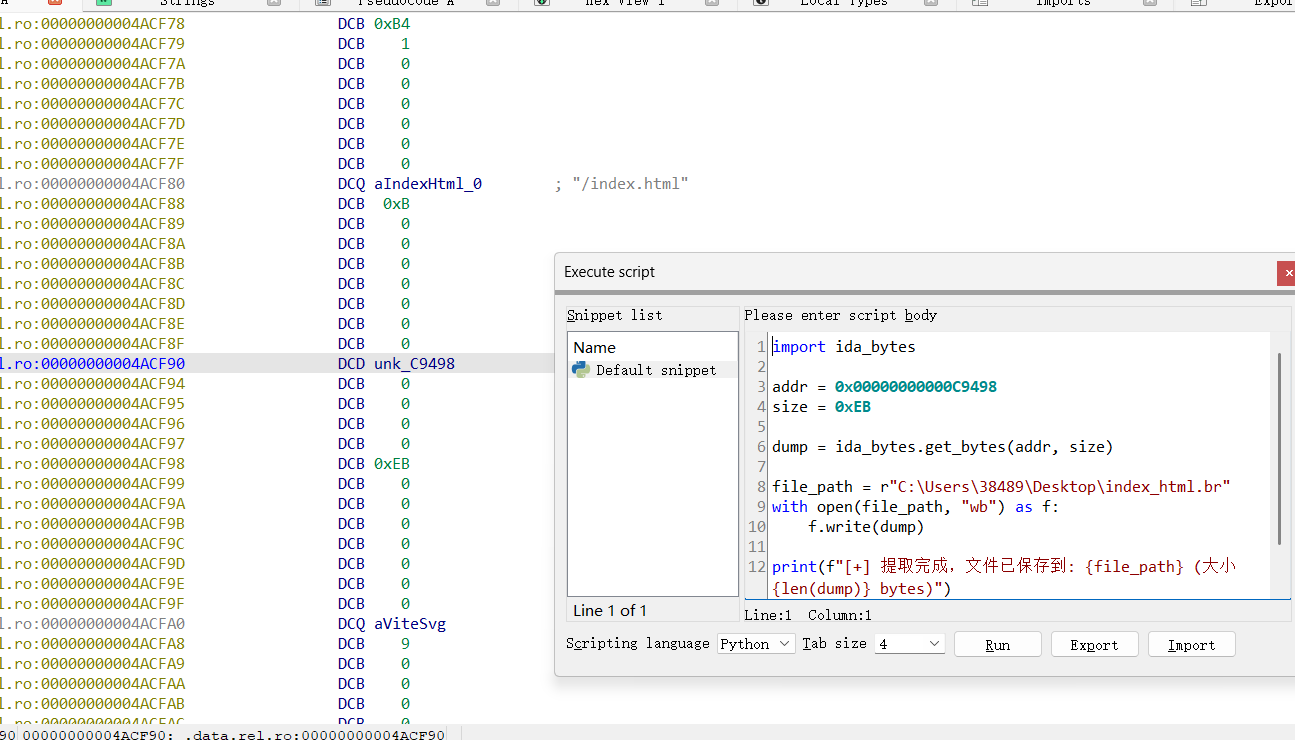
index内容

加载核心 JS,index-BsFf5qny.js 是打包后的 入口 JS 文件。负责启动 Vue 应用、挂载到 #app,以及通过 Tauri 的 API 调用 Rust 后端。
1 | |
和上述过程一样,继续搜索关键词,找到这个js文件,dump出来后解压
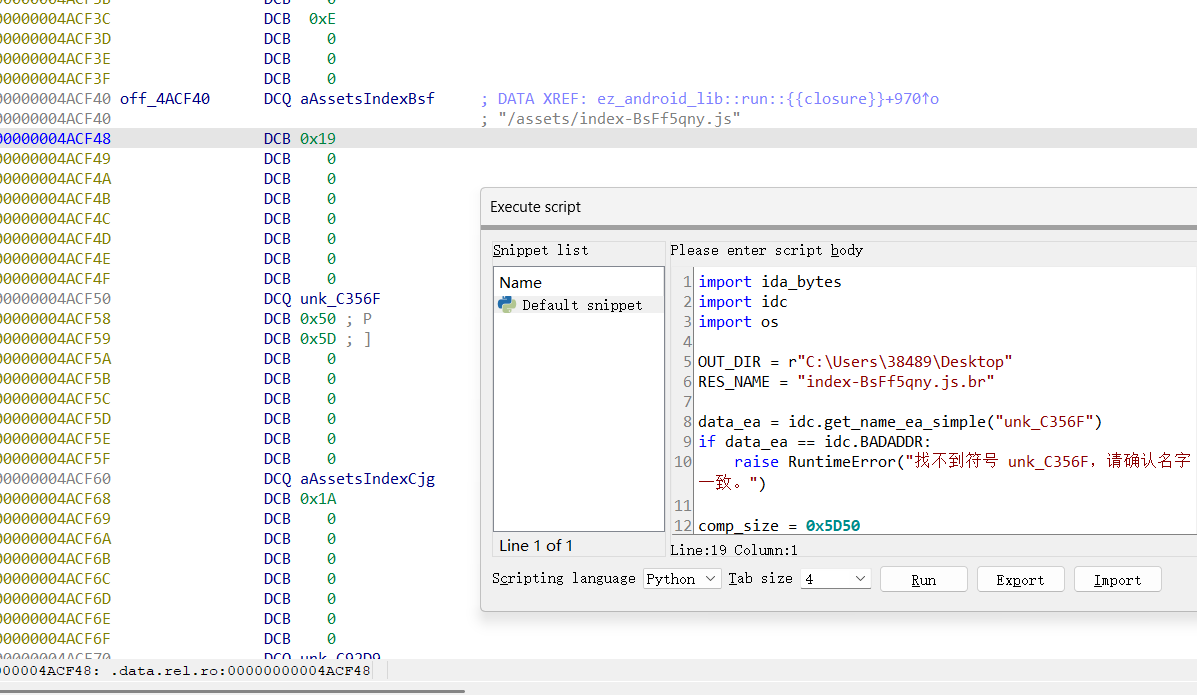
1 | |
1 | |
解压出来之后,找到关键点:js与后端rust交互,后端接口是greet,
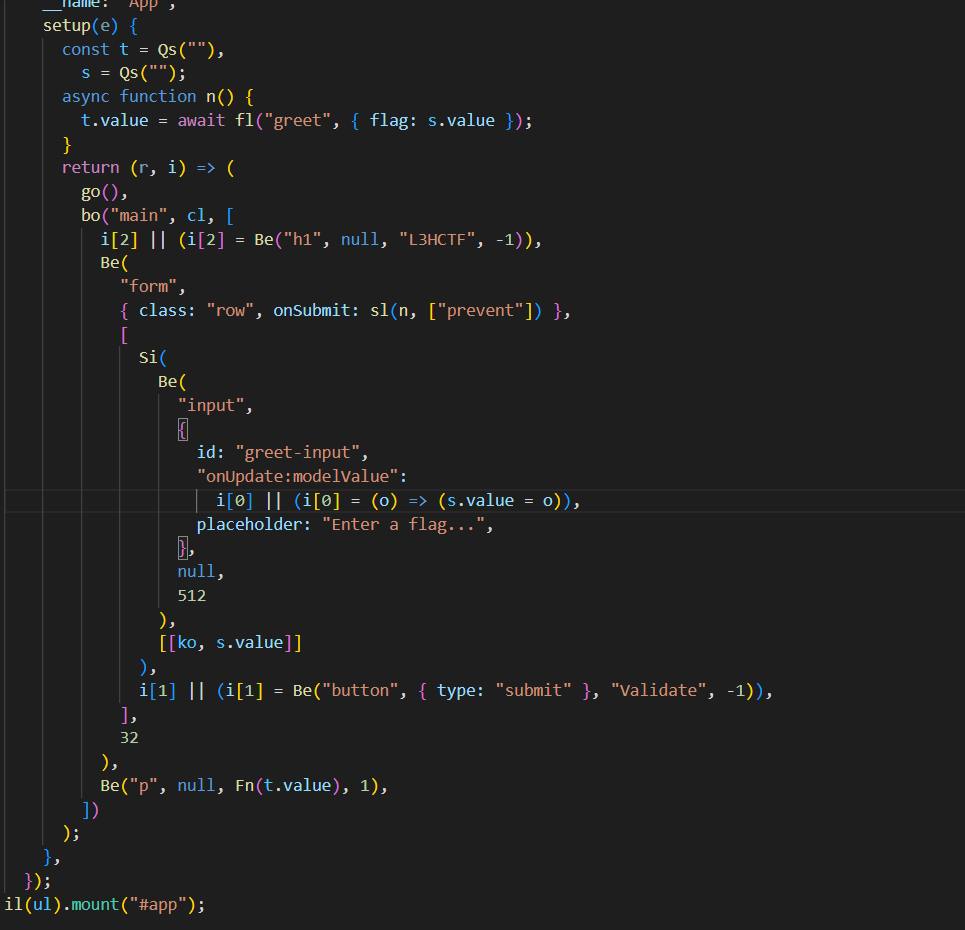
直接在ida里搜索greet,找到函数,就是主加密函数
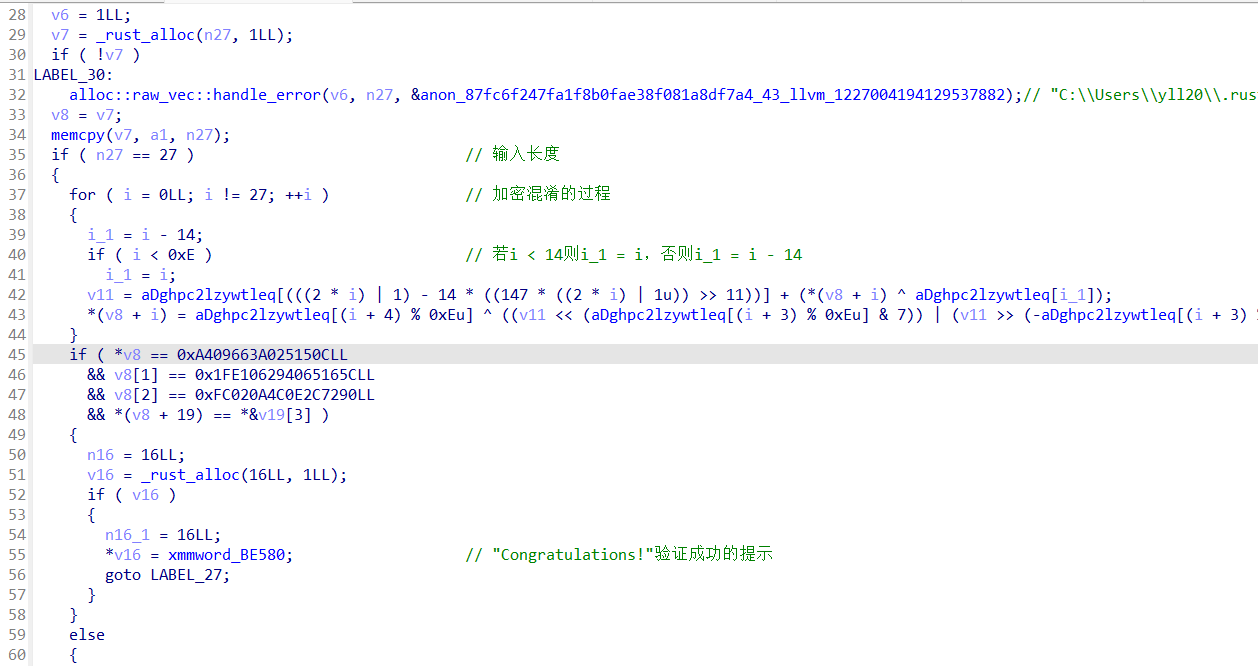
脚本
写脚本的时候还是要注意一下密文的提取,最后是v8的第19位与v19的第三位数据往后的八字节内容,当时脚本在密文这没好好分析,结果一直没出来,还是得注意一下
1 | |
完结撒花~
另附,学习这位师傅的tauri框架静态资源提取的方法https://blog.yllhwa.com/2023/05/09/Tauri%20%E6%A1%86%E6%9E%B6%E7%9A%84%E9%9D%99%E6%80%81%E8%B5%84%E6%BA%90%E6%8F%90%E5%8F%96%E6%96%B9%E6%B3%95%E6%8E%A2%E7%A9%B6/